Securing Access to an Azure Application With Terraform
This guide offers detailed steps for Udacity students working on the "Deploying a Web Server in Azure" project. It explains how to securely configure Network Security Group (NSG) rules in Azure using Terraform, ensuring robust network security and compliance with project requirements.

Overview
For students working on Udacity's project "Deploying a Web Server in Azure," correctly configuring Network Security Groups (NSGs) is a vital, yet often overlooked, aspect. This project involves deploying a simple web app across multiple VMs (2-5) connected to a load balancer, requiring stringent yet functional NSG rules.
A common mistake is leaving the network open to all traffic, posing significant security risks, or overly restricting access, rendering the site unreachable. According to a study, 20% of data breaches can be traced to misconfigurations, highlighting the importance of using NSG rules correctly.
Understanding NSG Rule Prioritization in Azure Network Security
Network Security Groups (NSGs) in Azure are crucial in managing network traffic to and from Azure resources. Here's an overview of NSG rules and how their priority works:
NSG rules control the flow of both inbound and outbound traffic to network interfaces (NICs), VMs, and subnets. They act as a firewall, providing security by filtering traffic based on IP address, port, and protocol.
The rules are prioritized to determine the order in which they are applied. The priority is a number between 100 and 4096. Lower numbers have higher priority, meaning they are processed before rules with a higher number. When traffic is evaluated, the first rule in the priority list that matches the traffic characteristics is applied.
By default, NSGs include a set of default rules. We can add Custom rules that override these default rules based on their priority. For instance, if a high-priority rule allows traffic, it will override a lower-priority rule that denies the same traffic type. Thus, understanding and correctly setting the priority of each rule is essential for effective network traffic management.
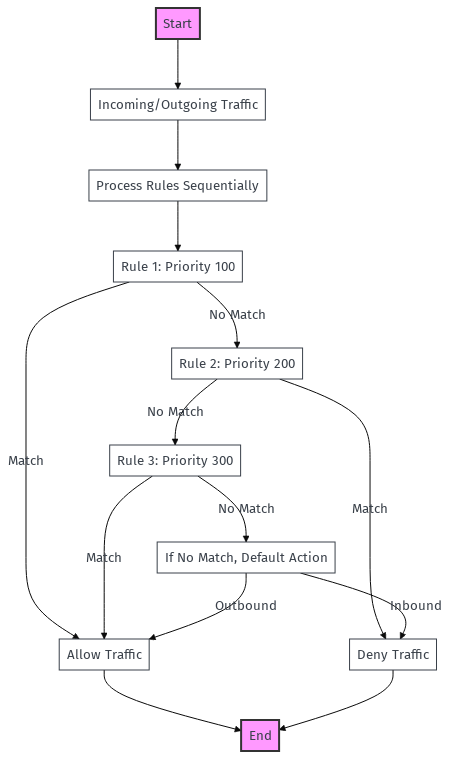
In summary, effectively managing NSG rules requires careful consideration of each rule's purpose and priority, ensuring that the rules work together to provide the desired network security and connectivity level.
Understanding azurerm_network_security_rule in Terraform
The azurerm_network_security_rule resource in Terraform allows us to create network security rules for our Azure Networks. Each attribute helps us tailor how traffic is managed in Azure's network interfaces, VMs, and subnets.
Key Attributes and Their Use Cases
resource_group_name: The name of the resource group where the NSG is located. This defines the organizational scope within Azure, where the NSG resides.network_security_group_name: The specific NSG to which the rule will be applied. This directly associates the rule with the intended NSG, ensuring that the defined security parameters are correctly enforced within that group.name: Uniquely identifies the rule. Useful for easy identification and management.priority: Determines the rule's execution order (100-4096). It is essential for controlling which rules take precedence.direction: Specifies if the rule is for inbound or outbound traffic, which is crucial for defining traffic flow direction.access: Defines whether the rule allows or denies traffic, central to security and access control.protocol: This specifies the protocol like TCP, UDP, or ICMP. For example, you might use TCP for web server traffic on port 80 or 443, while UDP might be used for streaming or VoIP applications.source_port_range&destination_port_range: These define the port ranges for the traffic. For instance, allowing traffic on ports 80 and 443 for a web server or restricting SSH access (port 22) to a specific IP range for security.
We can use each attribute to implement our security requirements precisely, enhancing our Azure environment's overall robustness. The Azure Terraform documentation is an excellent resource for comprehensive examples and deeper insights.
Implementing NSG Rules with Terraform in Azure
Correctly setting up NSG rules is vital for network security in Azure. Here, we explicitly define essential rules in Terraform, ensuring security against changes in Azure's default settings.
Key NSG Rules and Terraform Implementation
- Deny Inbound Traffic from the Internet: This rule explicitly blocks unsolicited inbound traffic, providing a solid security layer:
resource "azurerm_network_security_rule" "deny_inbound" {
name = "DenyInboundInternet"
priority = 4096
direction = "Inbound"
access = "Deny"
protocol = "*"
source_port_range = "*"
destination_port_range = "*"
source_address_prefix = "*"
destination_address_prefix = "*"
resource_group_name = "YourResourceGroupName"
network_security_group_name = "YourNSGName"
}
- Allow Intra-VNet Communication: Facilitates secure internal network operations:
resource "azurerm_network_security_rule" "allow_vnet_inbound" {
// ...configuration details...
resource_group_name = "YourResourceGroupName"
network_security_group_name = "YourNSGName"
}
resource "azurerm_network_security_rule" "allow_vnet_outbound" {
// ...configuration details...
resource_group_name = "YourResourceGroupName"
network_security_group_name = "YourNSGName"
}
- Allow HTTP Traffic to VMs from Load Balancers: Ensures your web services are externally accessible while maintaining security:
resource "azurerm_network_security_rule" "allow_http_loadbalancer" {
// ...configuration details...
resource_group_name = "YourResourceGroupName"
network_security_group_name = "YourNSGName"
}
- Associate your NSG with the VNet's subnet to implement these rules:
resource "azurerm_subnet_network_security_group_association" "example" {
subnet_id = azurerm_subnet.example.id
network_security_group_id = azurerm_network_security_group.example.id
}
- Please execute
terraform applyto activate these security measures in your Azure network.
Conclusion

In conclusion, the meticulous implementation of NSG rules using Terraform is a cornerstone in securing Azure environments.
We establish a robust security framework by explicitly defining critical rules, such as denying inbound traffic from the internet and managing internal network flows. This approach not only guards against potential changes in Azure's default settings but also grants us more control and clarity over our network's security posture.
Embracing this systematic approach to configuring NSG rules helps us achieve a secure, reliable, and efficient Azure deployment.
Addendum: A Special Note for Our Readers
I decided to delay the introduction of subscriptions. You can read the full story here.
If you find our content helpful, there are several ways you can support us:
- The easiest way is to share our articles and links page on social media; it is free and helps us greatly.
- If you want a great experience during the Chinese New Year, I am renting my timeshare in Phuket. A five-night stay in this resort in Phuket costs 11,582 € on Expedia. I am offering it in USD at an over 40% discount compared to that price. I received the Year of the Snake in style.

ReedWeek Timeshare Rental
- If your finances permit it, we are happy over any received donation. It helps us offset the site's running costs and an unexpected tax bill. Any amount is greatly appreciated:
- Finally, some articles have links to relevant goods and services; buying through them will not cost you more. And if you like programming swag, please visit the TuringTacoTales Store on Redbubble. Take a look. Maybe you can find something you like: